*Updated October 2022
In the words of former CISCO CEO John Chambers:
“There are two types of companies: those who have been hacked, and those who don’t yet know they have been hacked.”
Last year saw 50% more cyberattack attempts than the year before it. And no one is spared the danger - it’s estimated that cybercriminals can penetrate 93% of company networks. Clearly, strong digital security should be at the forefront of any company strategy today.
One of the most dangerous types of cyberattacks today is ransomware. But what can a company do to protect itself from this and similar cyber threats? And what are common ransomware threat vectors that can be anticipated?
We talked to data privacy expert Jose Belo to share valuable insights with you on the best practices in digital security today. We don’t mean to spoil the surprise, but you’ll find that protecting your company from various types of ransomware attacks requires building the best digital security defense and being aware of those attack vectors.
What is an attack vector?
A threat vector or attack vector is the path that a hacker uses to get the ransomware - malicious malware intended to hold data hostage until a ransom is paid - on your computer network (well, hopefully not your computer network). In other words, attack vectors are the way hackers establish their presence on a device or network.

But how do cybercriminals decide which threat vector to use? Ransomware attack vectors are selected based on the particular vulnerabilities of a given network. These cybersecurity vulnerabilities are called attack surfaces. So, once an agile hacker figures out the weakness of the IT infrastructure, they deploy the malware through the appropriate attack vector.
As we’re about to see, threat vectors are many and versatile. And when it comes to digital security, companies are like boats punctured with lots of little holes that allow water to seep through. The data security team has their work cut out for them - they have to keep plugging up the old holes, while at the same time, new ones are punctured.
This is not least of all because hackers are always developing new, creative malware and methods of attack. The types of ransomware and ransomware attack vectors vary from ones that require highly specialized tech knowledge to ones that employ plain old human manipulation.
What is the main vector of ransomware attacks and how does ransomware commonly spread to company networks?
Some of the most commonly used threat vectors to infect the devices in a network with ransomware include:
-
Email phishing: A target receives a misleading email with an attachment (PDF, ZIP, Microsoft Office) that urges them to download it. The attachment contains the malware that can spread throughout the network. The email may also just contain a link to a malicious website that either automatically downloads the malware or tricks the user into doing so. A newer version is vishing - which is the same but with a voice call.
-
SMS: It’s not just email but also SMS and other instant messaging, like WhatsApp, that can be used as threat vectors to send malicious software or links. Jose Belo advises that users always double-check the URL in an SMS, especially if it’s a login page of something like a bank asking for your account details - even if it’s not ransomware, you could be giving away account information for free.
-
Pop-ups and ads: Pop-ups and ads that seem to authentically belong to a brand may turn out to be phishing schemes that lead the user to a malicious website or cause them to download a piece of malware. They are quite a popular attack vector for ransomware, so be careful.
-
Unsecured remote desktop protocol connections: Microsoft’s proprietary RDP allows users to connect to the other devices within their network. If the network is online and not properly secured, hackers can gain access through brute-force attacks and hold data or access to the network for ransom.
-
Social engineering: This is exactly what it sounds like: the hacker works the person, not the computer. A person may be tricked into revealing their password during a conversation or even wiring money to someone they believe is working for the company. For instance, in 2019, hackers used AI to mimic the voice of a parent company’s CEO to get a transfer of $243,000.
This is an example of using deepfakes in cybercrime, and trust us when we say that deepfakes are becoming increasingly hard to identify as such. In another attack vector example of social engineering, hackers managed to penetrate the digital security defenses of the RSA in 2011 when an employee received a simple Excel spreadsheet and opened it, releasing malware to the local machine that then spread throughout the network.
We will later see why educating employees thoroughly about digital security practices is key in cybersecurity. For instance, in this case, it was concluded that:
“That initial point of entry onto RSA’s network, F-Secure’s Hirvonen would later point out in his own analysis, wasn't particularly sophisticated. A hacker wouldn’t have even been able to exploit the Flash vulnerability if the victim had been running a more recent version of Windows or Microsoft Office, or if he’d had limited access to install programs on his PC—as most security administrators for corporate and government networks recommend, Hirvonen says.”
Since we’re not all about fear-mongering, let’s move on to how you can protect yourself from ransomware attack vectors with insights from Jose.
Digital security 101 with Jose Belo: Protecting your network from ransomware attack vectors
How can you make your network foolproof against ransomware attack vectors? The most truthful answer we can give you is that you cannot. But that doesn’t mean that you can’t set up defenses against various types of ransomware and thoroughly minimize the chances that malware reaches your network through any attack vector.
In fact, Belo says that in the case of digital security, the best offense is a good defense. We need to create as many barriers as possible. He says:
“If you have 24-hour security, guard dogs, windows, and doors closed, but you get robbed anyway - OK, you did everything you could, you prepared. But if you leave the doors and windows open and you get robbed, well - you had it coming. If you leave your keys in an unlocked car and it's stolen, it’s on you.”
And this is the same logic that cybersecurity insurance firms follow. It’s well-advised to get CS insurance when there’s a lot at stake, and it may keep your mind at ease when you remember ransomware attack vector examples and past, notable cybercrimes. However, if a CS insurance firm finds that you did not take the necessary steps to fend off potential attacks, they won’t reimburse you for the losses.
According to Belo, good digital security includes both technical or technological measures such as controlled access, zero trust, automation, etc., as well as organizational, or human measures such as training, enacting policies and procedures, and so on, so that each employee knows how to act safely. When you combine these two approaches, you reduce the number of attack surfaces, i.e. vulnerabilities, and thus potential ransomware attack vectors.
Finally, data protection is threefold and includes information security, cybersecurity, and personal data protection. A strong digital security infrastructure that contains all three will satisfy the CIA triad model: Confidentiality, Integrity, and Availability.
That’s the general idea, so let’s get into the specifics.
Run scenarios for digital security
Belo says that one of the main things a company needs to do is run scenarios with their CSIRT - Computer Security Incident Response Team. The CSIRT is like a second line of defense, the first being your digital security measures and trained employees. If those are in order, you don’t have to worry about ransomware attack vectors - as you’ve left no gaps for them.
The CSIRT goes through different ransomware attack vectors or other cybersecurity breaches to test their digital security and practice responding to it. This is called penetration testing. What’s more, after each test run or - God forbid - actual break-in, digital security teams should do an autopsy or post-mortem where they identify what went wrong and what should be done differently next time around.
Some companies may hire white-hat hackers to see a breach and help them identify the network’s vulnerabilities.
Don’t put all your eggs in one basket: Data security
Data is currency, and that’s exactly what hackers are after in the case of ransomware. And it’s not just with ransomware examples that we need to worry about data - even power outages can cause website downtime, and website downtime can lose you customers. What this means is that every company needs backups of their data - backups being plural. So it’s not just “don’t put all your eggs in one basket,” it’s actually - “don’t even put all your eggs in only two baskets.”
As servers can be breached in various ways, Jose says cloud storage is a good place for additional backups. He cites an example of two servers, the main server and the backup server, sitting next to one another in the server room. What happens if the power goes out? What happens if someone gains access to the server room? What happens if there’s a flood and it's in the basement? The backup is just as endangered as the main server.
Keep in mind, though, that as ransomware becomes more sophisticated, the cloud isn’t fully safe, either. Smaller companies can mitigate the threat by using a huge cloud provider with lots of resources that ensure better safety. In any case, Belo emphasizes that companies need to encrypt their data. This way, even if a malicious party gains access to it, they won’t be able to do anything with the gibberish that actually hides precious information.
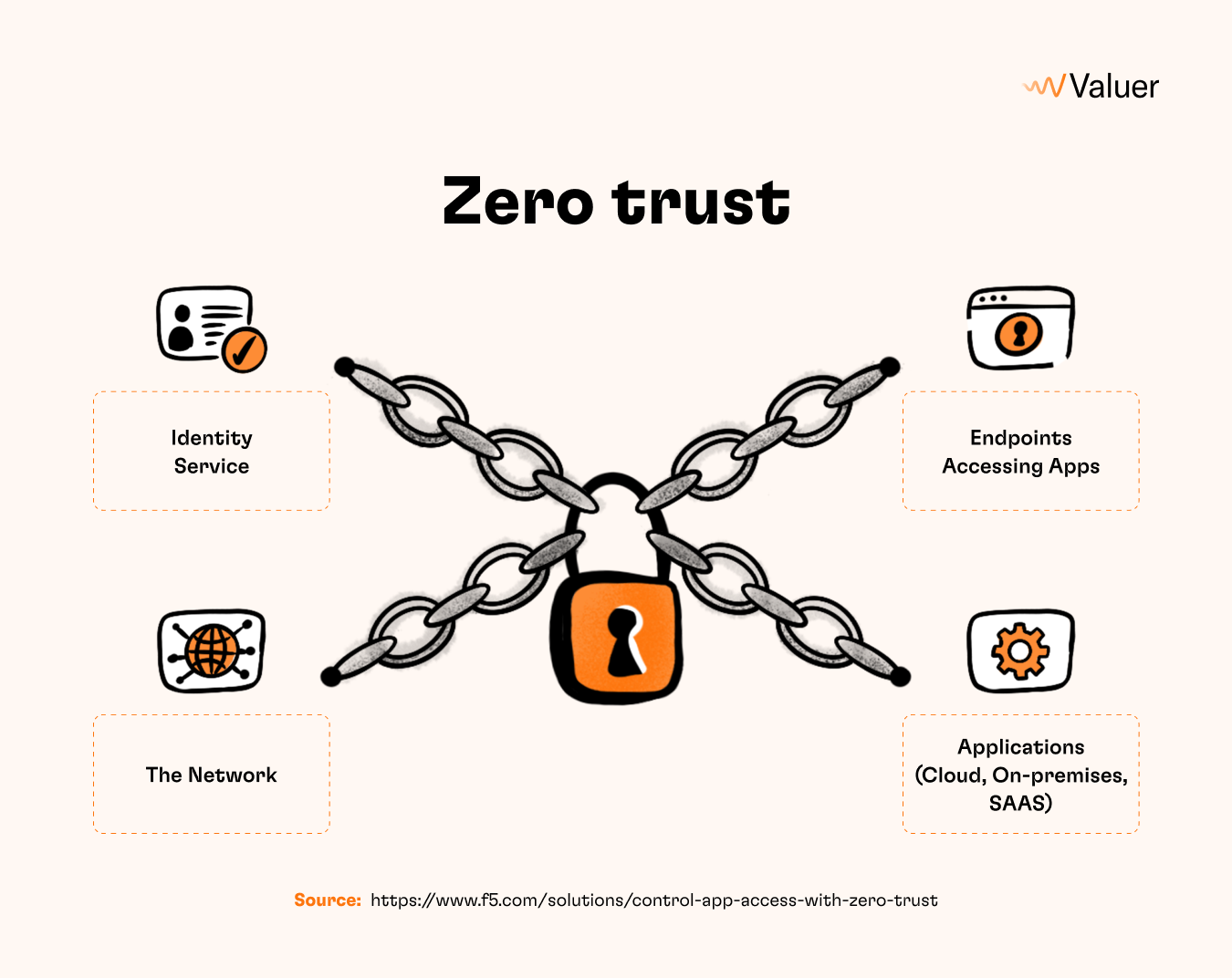
Zero trust network access
On the subject of implementing all the right tech measures, zero trust should be every company’s goal. Zero trust network access as a digital security framework continuously validates all users both within and outside the network in order for them to gain and regain access to data and apps. This significantly reduces the margin of error for both remote and local access and “secures an organization by eliminating implicit trust.”
Automation
Automation is an increasingly used and important element of digital security in general, so naturally, it’s key in reducing ransomware threat vectors. In general, automation means integrating AI and ML in your digital security framework in order to anticipate attack vectors, patch up vulnerabilities, etc. Antimalware programs are actually a type of CS automation.
Zero trust network access is also an automated process, and automation in digital security needs to be paired with penetration testing to have both the machines and the humans ready.
The human factor: Train your employees on threat vectors
We already saw how a single employee opening a spreadsheet from an email got the biggest CS company in the world in a world of trouble. This is why it’s of utmost importance for not only the IT team but everyone in your company to be well-versed in cybersecurity policies and protocols.
In the case of the deepfake voice call from the company’s CEO demanding that money be immediately wired to a certain account, an employee should know to say no even to the boss without the appropriate protocols and credentials. Belo says this is a “CEO scenario” where employees learn to say no and fight their urge to follow the boss’s orders because, in today’s age of lightspeed advances in technology, it’s hard to be sure it’s actually your boss on the phone or even on a video call.
Some companies may choose to test their employees just as they would run pen tests. You may send emails from dubious sources and with dubious content and check whether they follow protocol or throw caution to the wind. Another important step is keeping all software updated with the latest patches. Again, with the case of the RSA breach, if the device hadn’t lacked the latest software update, the malware wouldn’t have made it onto the company network.
Why startups need good digital security infrastructures
Jose revealed that even young startups are in great need of good digital security. Beyond the obvious reasons, startups need this in the form of CS compliance and certification when they’re being evaluated by investors and larger partners.
As supply chain attacks are becoming more and more common - cases where cybercriminals target smaller companies to reach the big guys and deploy the ransomware there - parent companies and partners are increasingly wary of who they do business with. They can’t jeopardize their digital security over an investment opportunity or partnership, so lax security can have a high cost for a startup in many ways.
So, big companies vet smaller ones to see if they have training manuals, CS policies, certifications, etc. A lack of proper digital security may impact the decision of whether they want to make a contract with a startup at all.
CSaaS (CyberSecurity-as-a-service)
Businesses that lack the resources to put together their own CS team can hire a CSaaS firm to do it for them. As the name suggests, a CSaaS firm outsources digital security management to a third-party vendor. The services performed by a CSaaS company may include digital security consultations, checks, pen testing, employee training, software and antivirus updates, compliance, etc.
The emergence of such companies leaves little room for excuses regarding weak digital security. Companies that lack the resources for their own CS team should be able to invest in CSaaS as the cost is significantly lower.
The bottom line: The cost of doing nothing
Jose Belo repeats that it all boils down to this: “what’s the cost of doing nothing?” Data is increasingly valuable, which is why it’s the main target of ransomware attacks. So if a company doesn’t protect its data, what does that tell investors? What does it tell customers? If you don’t protect data, you’re not protecting the company. It loses a company its reputation, funding, and perhaps most important of all, the trust of its customers.
So while cyberattacks happen all the time, what matters is how we prepare for them and how we deal with them. If a company does all it can and still gets attacked, it has a good explanation, so people are much more likely to understand and forgive the incident.
However, if a company lacks good digital security, gets attacked, and loses - for instance - the personal data of its users, there’s no excuse. And moreover, how prepared the digital security architecture of a firm is, is the difference between whether they can shrug off an attack like it’s nothing or whether that attack will be lethal to the company.
[Related Article - How to Find Innovative Cybersecurity Startups]
But the matter of cybersecurity may soon be a directive rather than a suggestion. Jose reveals that governments and supranational organizations like the EU are very much aware of cyber threats, and they are taking action to prevent them through new policies like the NIS2 directive. In the US, the position of CISO (Chief Information Security Officer) may soon become mandatory.
Regardless, any company worth its salt should do everything within its power to protect its integrity and the trust of its customers. After all, the cost of doing nothing is far too high.
.png?width=103&height=103&name=Untitled_Artwork%20725%20(2).png)